I have been in DevOps related jobs for past 6 years dealing mainly with Kubernetes in AWS and on-premise as well. I spent quite a lot …
 :date_long | 1 min Read
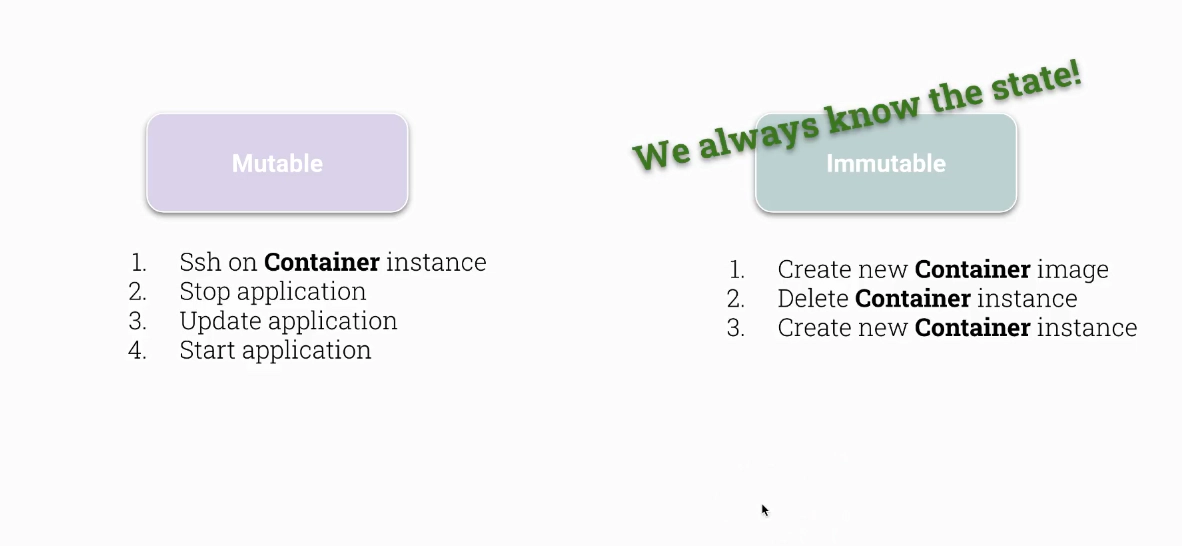
:date_long | 1 min ReadCKS Immutability of containers at runtime
- advanced deployment methods
- easy rollback
- more reliability
- better security (on container level)
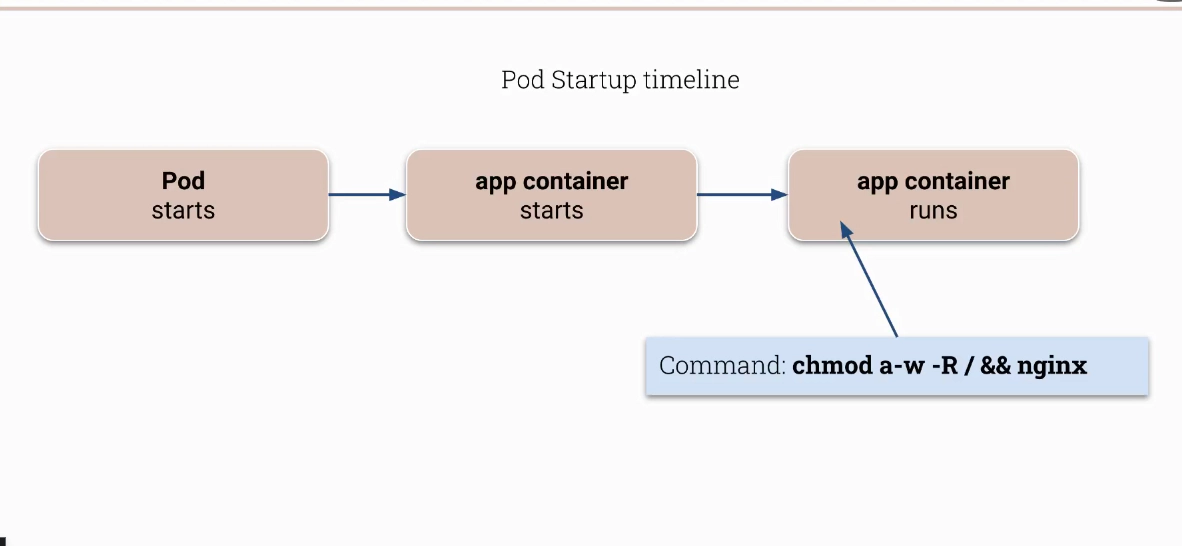
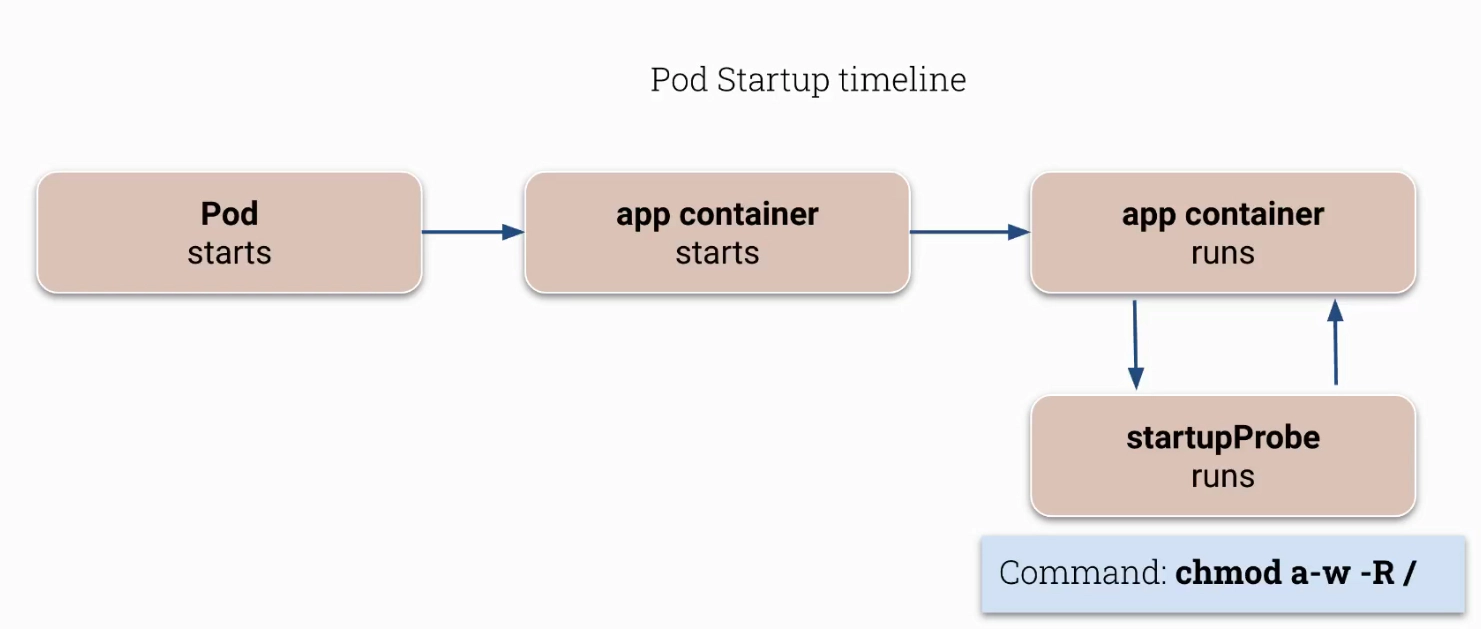
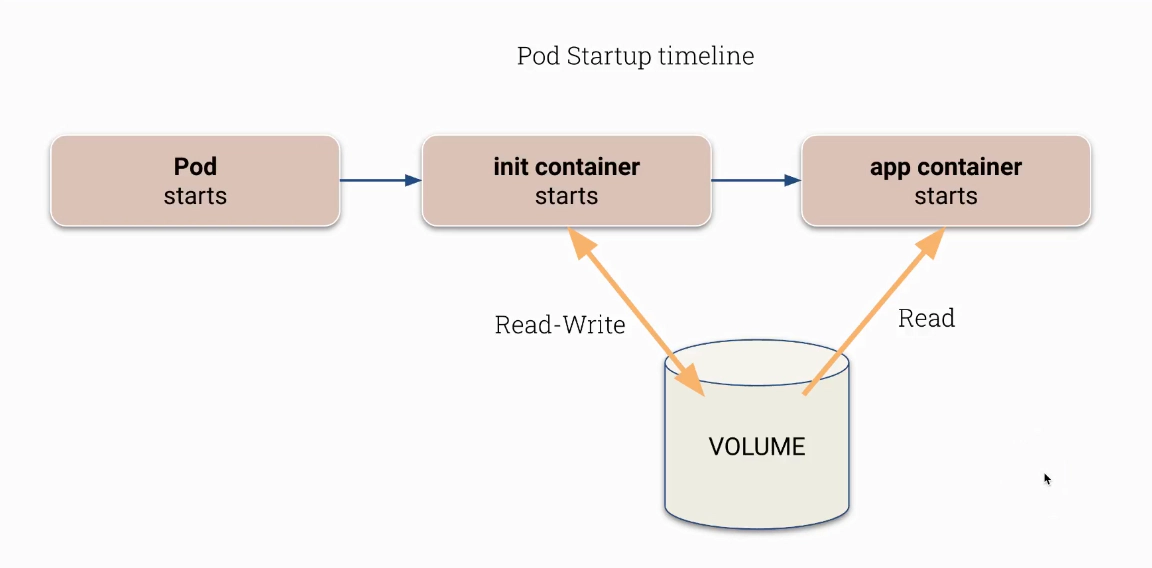
Interesting example of how ‘‘startupProbe’’ can be used to make container a bit more secure
root@cks-master:~# cat immutable.yaml
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: immutable
name: immutable
spec:
containers:
- image: httpd
name: immutable
resources: {}
startupProbe:
exec:
command:
- rm
- /bin/bash
initialDelaySeconds: 1
periodSeconds: 5
dnsPolicy: ClusterFirst
restartPolicy: Always
status: {}
ReadOnlyRootFilesystem example
cat immutable.yaml
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: immutable
name: immutable
spec:
containers:
- image: httpd
name: immutable
securityContext:
readOnlyRootFilesystem: true
volumeMounts:
- name: pid
mountPath: "/usr/local/apache2/logs/"
volumes:
- name: pid
emptyDir: {}
dnsPolicy: ClusterFirst
restartPolicy: Always
status: {}
If you come from Docker world
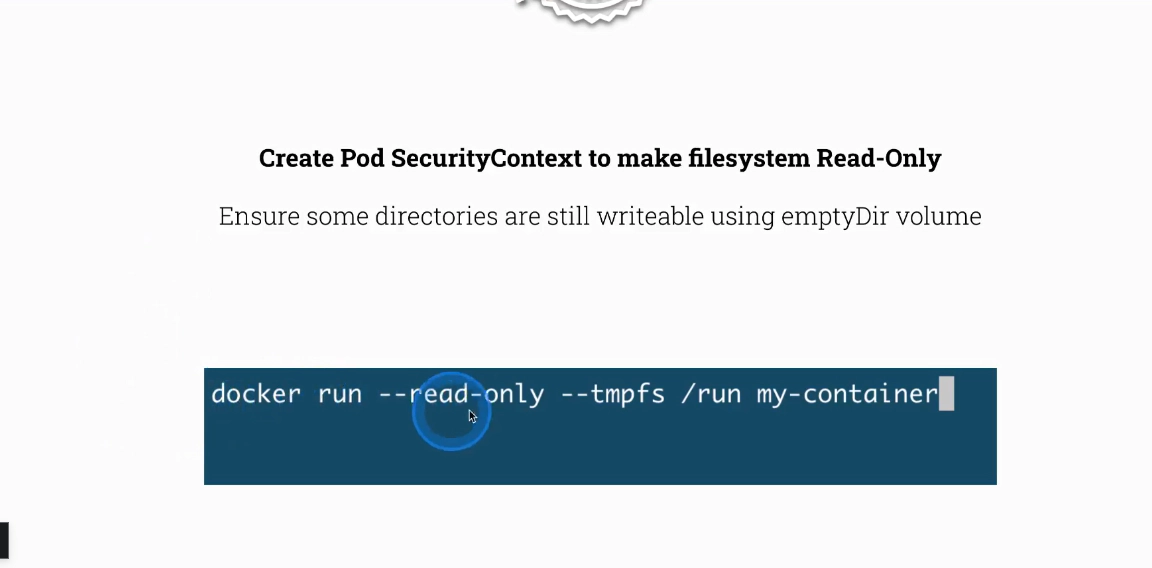
Task
Generate pod receip
k run pod-ro -n sun --image=busybox:1.32.0 --dry-run=client -oyaml --command -- sh -c 'sleep 1d' > pod.yaml
controlplane $ cat pod.yaml
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: pod-ro
name: pod-ro
namespace: sun
spec:
containers:
- command:
- sh
- -c
- sleep 1d
image: busybox:1.32.0
name: pod-ro
resources: {}
securityContext:
readOnlyRootFilesystem: true
dnsPolicy: ClusterFirst
restartPolicy: Always
status: {}